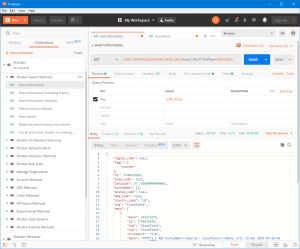
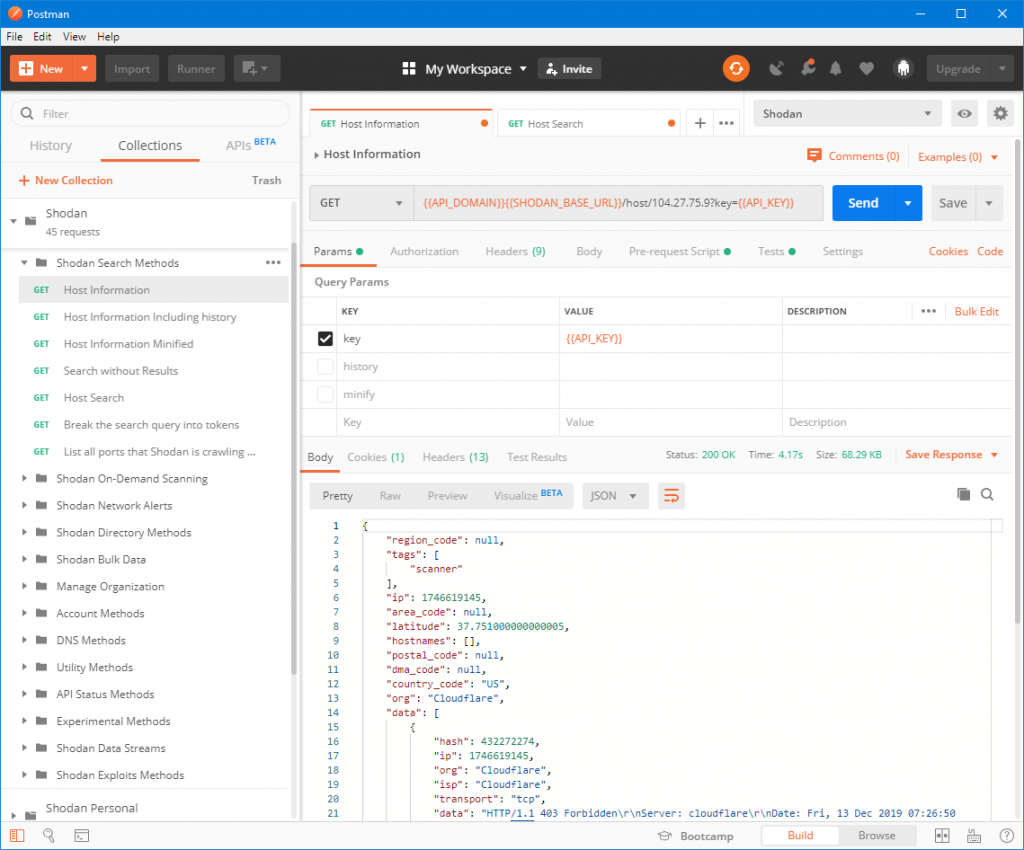
The Christmas holidays are coming and to those of you who feel like doing something adventurous: there is now a new way to visit the dark caverns of the internet. We created an exciting combination of two existing services that make this trip possible: A Postman collection of all the currently available Shodan API calls.…
Read MoreA few months ago, a new vulnerability was found in jQuery, affecting all existing versions of jQuery. It was fixed only in the new version 3.4.0.The SNYK website has a lot of detailed information about this ‘Prototype Pollution’ vulnerability, so I won’t go into that here. For those interested, follow this link : https://snyk.io/vuln/SNYK-JS-JQUERY-174006 What…
Read MoreAt BitnessWise we recently did a review of a few Two Factor Authentication (2FA) plugins for WordPress. First we selected some candidates based on usability and free-version features and after that performed a technical review of the plugin. This revealed a vulnerability we’d like to discuss in this post for future reference and to better…
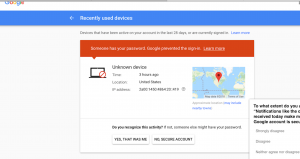
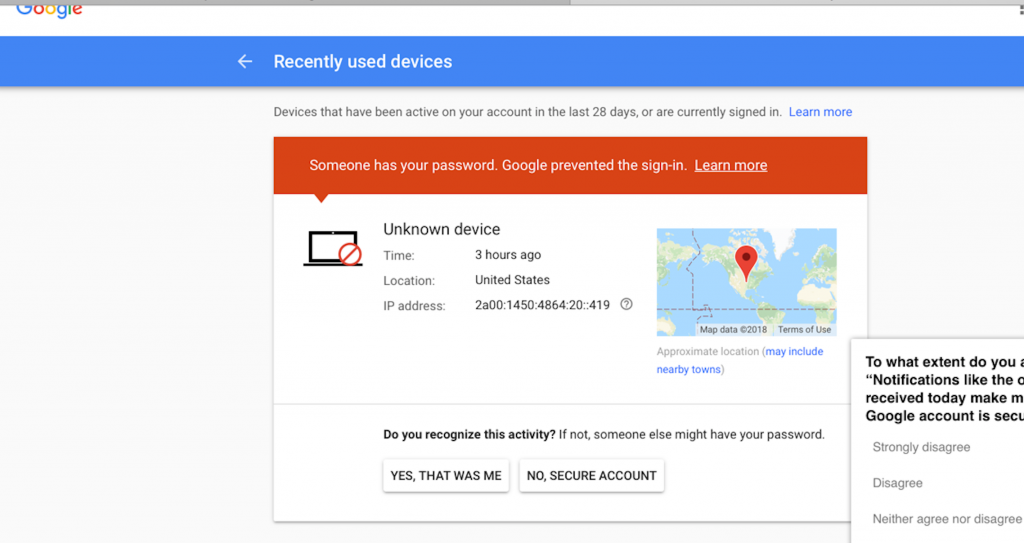
Read MoreLast weekend, almost exactly between April Fools’ Day and Halloween, Google played a prank and scared us! If you have used Gmail on different devices, you probably know the kind of message you get when you log in from a different device. Additionally, you might be presented with a security question if Google doesn’t trust…
Read MoreShodan Postman Collection
The Christmas holidays are coming and to those of you who feel like doing something adventurous: there is now a new way to visit the dark caverns of the internet. We created an exciting combination of two existing services that make this trip possible: A Postman collection of all the currently available Shodan API calls….
Mitigating CVE-2019-11358 in old versions of jQuery
A few months ago, a new vulnerability was found in jQuery, affecting all existing versions of jQuery. It was fixed only in the new version 3.4.0.The SNYK website has a lot of detailed information about this ‘Prototype Pollution’ vulnerability, so I won’t go into that here. For those interested, follow this link : https://snyk.io/vuln/SNYK-JS-JQUERY-174006 What…
Two Factor Authentication Cross Site Request Forgery (CSRF) vulnerability (CVE-2018-20231)
At BitnessWise we recently did a review of a few Two Factor Authentication (2FA) plugins for WordPress. First we selected some candidates based on usability and free-version features and after that performed a technical review of the plugin. This revealed a vulnerability we’d like to discuss in this post for future reference and to better…
We prevented a sign-in attempt
Last weekend, almost exactly between April Fools’ Day and Halloween, Google played a prank and scared us! If you have used Gmail on different devices, you probably know the kind of message you get when you log in from a different device. Additionally, you might be presented with a security question if Google doesn’t trust…







 .
.